1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| #include <stdio.h>
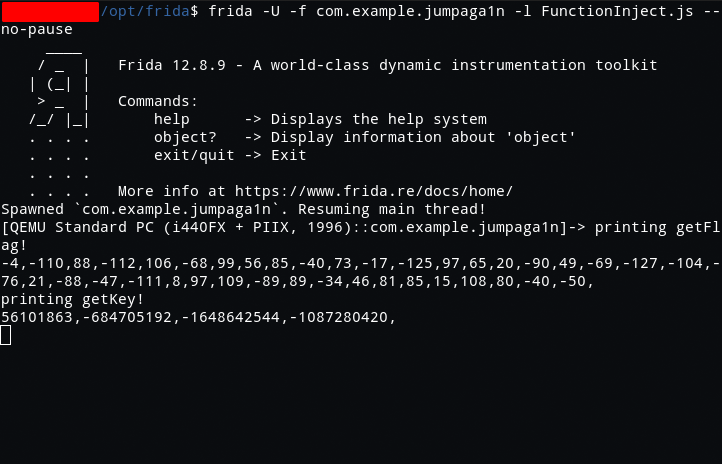
char getFlag[]={-4,-110,88,-112,106,-68,99,56,
85,-40,73,-17,-125,97,65,20,
-90,49,-69,-127,-104,-76,21,-88,
-47,-111,8,97,109,-89,89,-34,
46,81,85,15,108,80,-40,-50};
int getKeys[]={56101863,-684705192,-1648642544,-1087280420};
void decrypt(unsigned int* v, unsigned int* key) {
unsigned int l = v[0], r = v[1], sum = 0, delta = 0x9e3779b9;
sum = delta *32;
for (size_t i = 0; i < 32; i++) {
r -= ((l << 4) + key[2]) ^ (l + sum) ^ ((l >> 5) + key[3]);
l -= ((r << 4) + key[0]) ^ (r + sum) ^ ((r >> 5) + key[1]);
sum -= delta;
}
v[0] = l;
v[1] = r;
}
int main(int argc, char const *argv[])
{
//test
unsigned int * sec=(unsigned int*)getFlag;
for(int i =0;i<12;i+=2){
decrypt(&sec[i],(unsigned int*)getKeys);
}
for(int i=0;i<48;i++){
printf("%c",getFlag[i]);
}
return 0;
}
|